Trusted by thousands of companies worldwide
How it Works
How Passwiser’s Identity Platform Works
Streamline authentication and security with real-time detection, end-to-end encryption, and automated incident response.
Advanced Detection
Continuously monitor all authentication flows and network events for suspicious activities.
Robust Data Encryption
Encrypt all sensitive tokens and user data at rest and in transit using industry-standard protocols.
Automated Response
Instantly enforce security policies and notify your team the moment an incident is detected.
Key Features
In-Depth Explanation of Our Identity & Access Management Features
Empower your applications with secure authentication, flexible login methods, and enterprise-grade access controls.
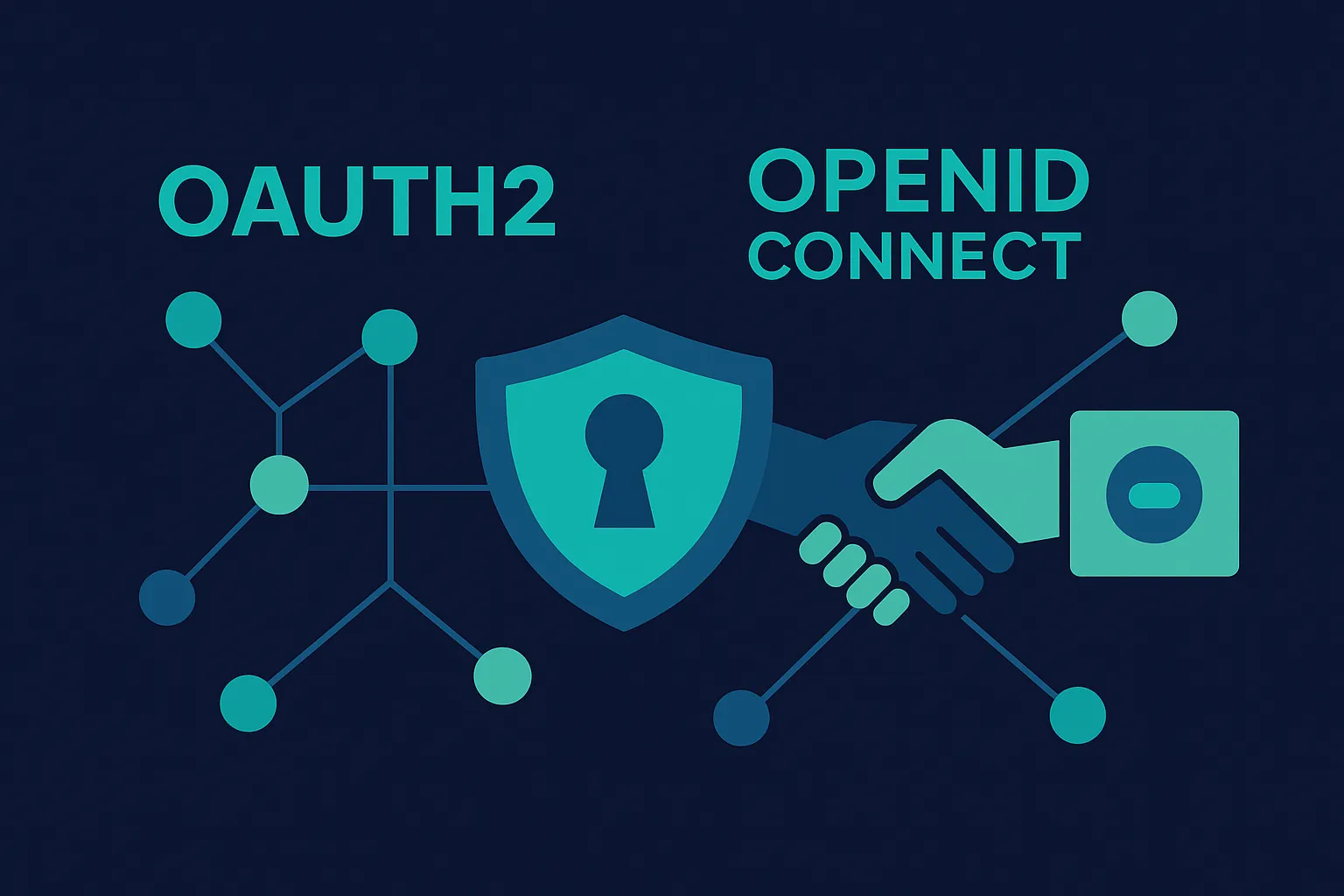
Flexible Authentication Protocols (OAuth2 & OIDC)
Implement industry-standard OAuth2 and OpenID Connect for secure, federated authentication across all your services.
Diverse Login Methods
Support social-media providers (Google, Facebook), Web3 wallets, magic-links, and passwordless authentication for seamless user experiences.

Enterprise-Grade Security Controls
Enable single sign-on (SSO), multi-factor authentication (MFA), and CAPTCHA protection to safeguard your applications against unauthorized access.
Learn More Details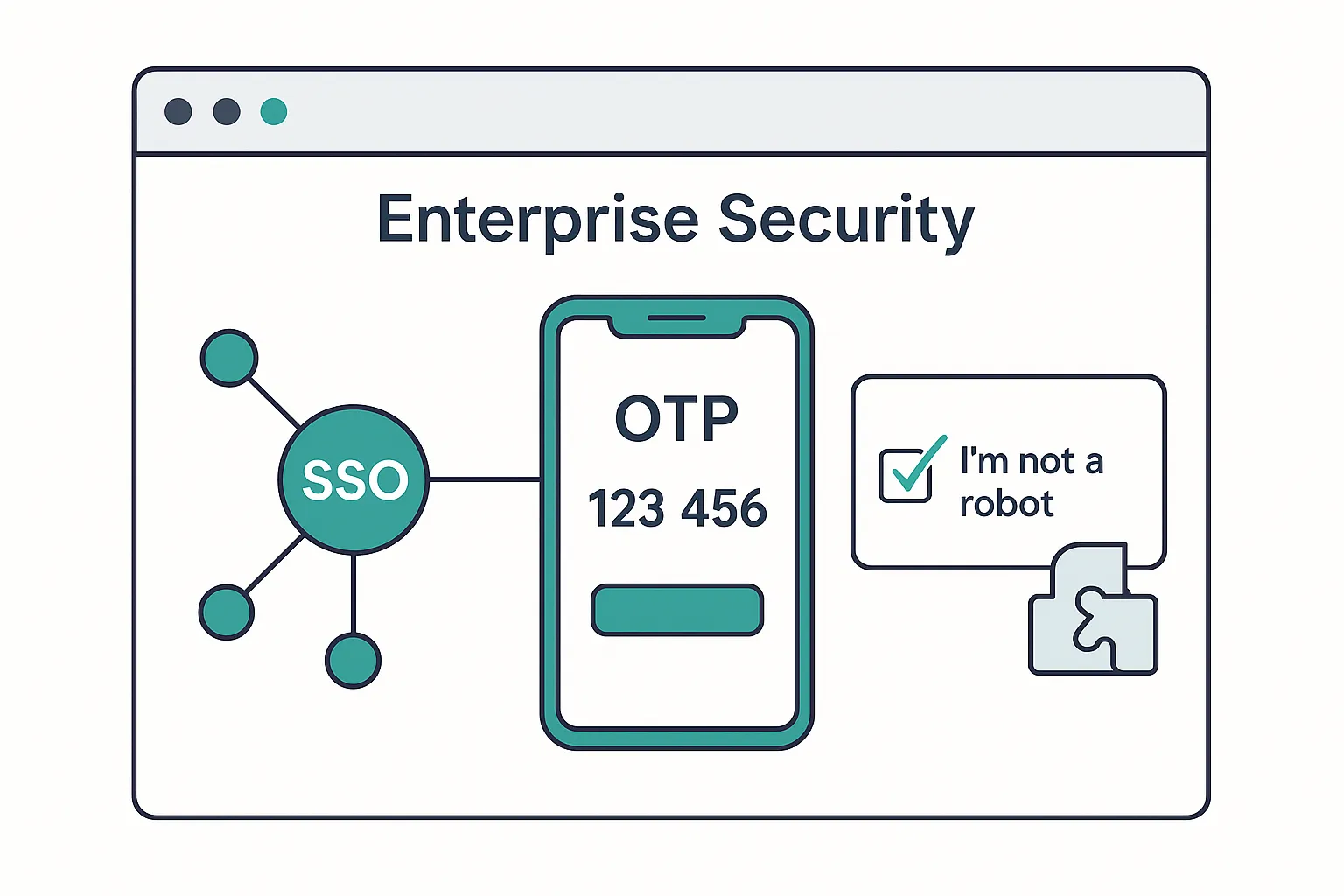
Essential Feature
Discover the Features That Make Passwiser Stand Out.
Streamline authentication workflows and strengthen security controls with our comprehensive identity platform.

Centralized Activity Dashboard
Set thresholds for authentication and security metrics with real-time alerts to keep you informed of critical events.
Detailed Audit Logs
Capture every authentication event—logins, token exchanges, and permission changes—for full visibility.
Anomaly Detection
Automatically flag unusual login times, IP addresses, or access patterns to catch threats early.
Comprehensive Security Insights
Gain a high-level summary of your identity security posture across protocols, providers, and applications.
-
End-to-End Encryption
Protect tokens and user data in transit and at rest with military-grade encryption standards.
-
Role-Based Access Control
Define granular permissions and enforce multi-factor authentication to minimize unauthorized access.
-
Compliance Audits
Automate periodic reviews of user access and configuration settings to ensure policy adherence.
Features Explained
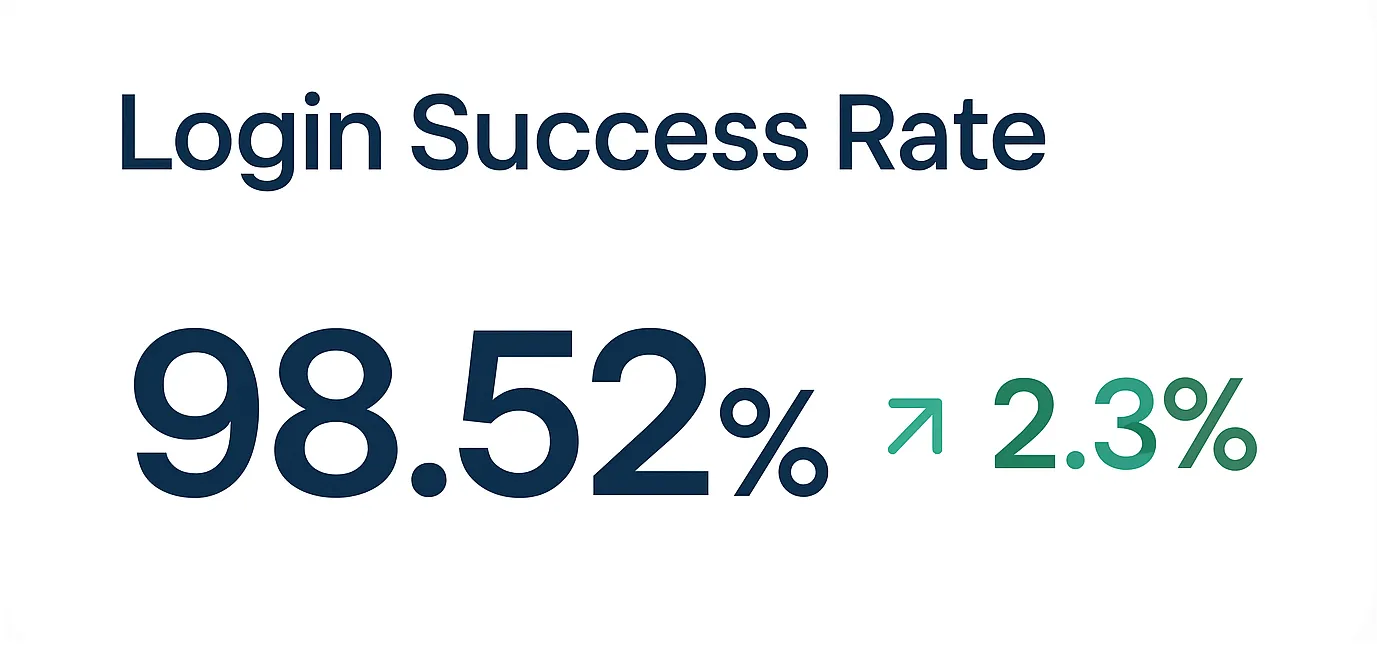
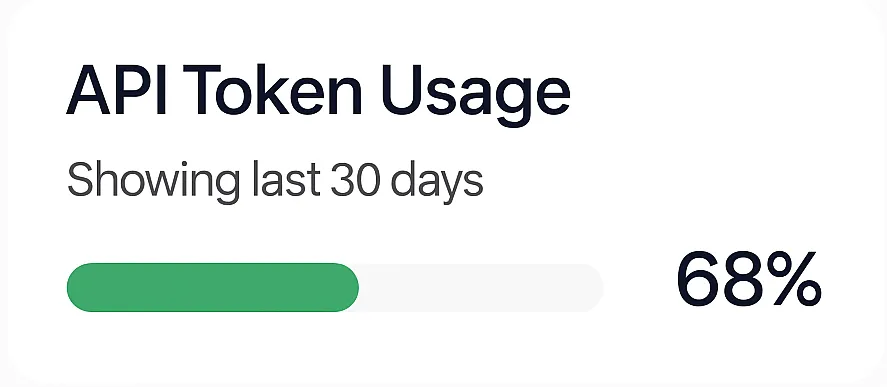
Live Identity & Access Metrics at a Glance
Visualize authentication health, user behavior, and security posture in real time with our interactive dashboard.
Security Status Indicator
Displays the current security status of your organization with a clear color-coded indicator.
User Activity Monitoring
Highlights the most frequently accessed sensitive files or databases and the users involved, ensuring transparency and control over critical data.
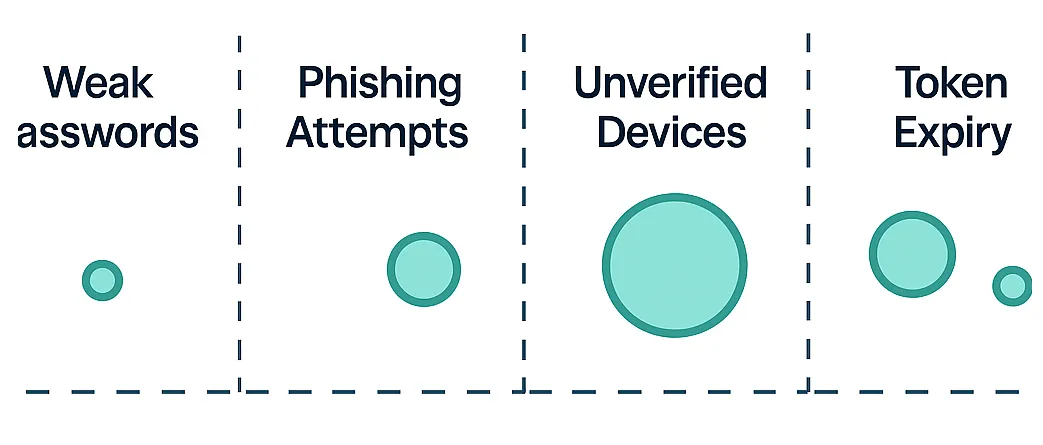
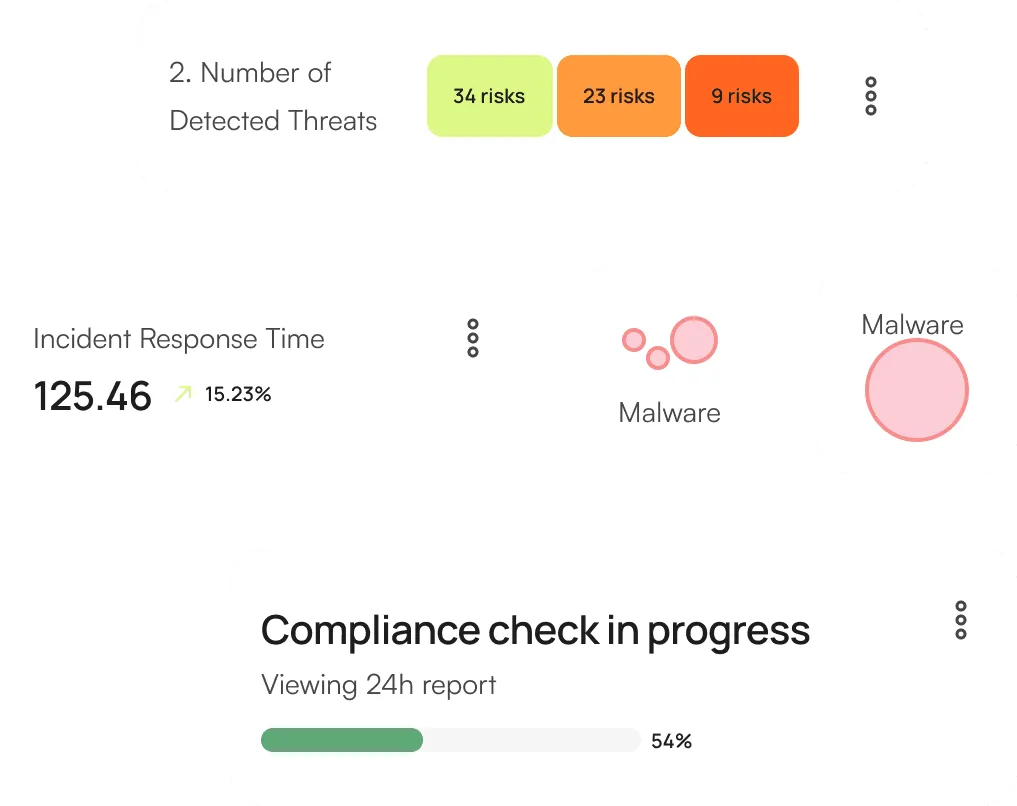
Threat Landscape Overview
Breaks down the threats by type (e.g., phishing, malware, ransomware) to give a detailed overview of the threat landscape.
Data Access Monitoring
Highlights the most frequently accessed sensitive files or databases and the users involved.
Incident Management
Lists the number of active security incidents currently being addressed.
Compliance Monitoring
Our system continuously monitors your network and data environments for any suspicious activities.